A Simple Guide to the Updated NIST 2.0 Cybersecurity Framework

Keeping up with security threats is a challenge for businesses of all sizes. Between February and March of 2024, global security incidents rose by 69.8%. To protect your organization, it’s crucial to adopt a structured approach to cybersecurity. The National Institute of Standards and Technology (NIST) developed a Cybersecurity Framework (CSF) to help organizations manage […]
10 Easy Steps to Building a Culture of Cyber Awareness

Cyberattacks are a major risk in today’s digital age. Phishing emails, malware, and data breaches can severely harm businesses and personal lives. A lot of these threats enter a company’s network because of employee mistakes. Often, it’s a lack of cyber awareness about cybersecurity. People unknowingly click on phishing links or create weak passwords, making […]
Don’t Risk It! Why You Shouldn’t Skip Vulnerability Assessments

Cyber threats are a constant challenge for business owners, as hackers are always finding new ways to take advantage of system vulnerabilities. A proactive stance on cybersecurity is crucial for businesses of all sizes, and one key aspect of this strategy is conducting regular vulnerability assessments. This process systematically identifies and prioritizes weaknesses in your […]
7 Common Pitfalls When Adopting Zero Trust Security

Zero Trust security is revolutionizing the cybersecurity landscape by shifting away from traditional perimeter-based models. This approach ensures that every connection attempt is constantly verified before granting access to resources, reinforcing security at every level. 56% of global organizations say adopting Zero Trust is a “Top” or “High” priority. This strategy provides substantial security benefits, […]
Here Are the Top CyberSecurity Threats and Trends to Prepare for in 2024

As cybersecurity threats continue to evolve rapidly, staying proactive is essential. News reports highlight the rise in cybersecurity threats and trends each week, making it critical to protect sensitive data. The sophistication and frequency of data security risks are increasing, and the security landscape must adapt accordingly. In 2024, we can anticipate both exciting advancements […]
Google & Yahoo’s New DMARC Policy Shows Why Businesses Need Email Authentication… Now

Have you been hearing more about email authentication lately? There’s a good reason for that: phishing is a major security threat. It continues to be the leading cause of data breaches and security issues, and this has been ongoing for years. Google and Yahoo, two of the biggest email providers globally, have rolled out a […]
Beware of Deepfakes! Learn How to Spot the Different Types

Have you ever watched a video of your favorite celebrity saying something shocking, only to later find out it was fake? Or maybe you’ve gotten an urgent email that seemed to be from your boss, but something felt wrong? This is the world of deepfakes. It’s a fast-growing technology that uses artificial intelligence (AI) to […]
10 Most Common Smart Home Issues (and How to Fix Them)
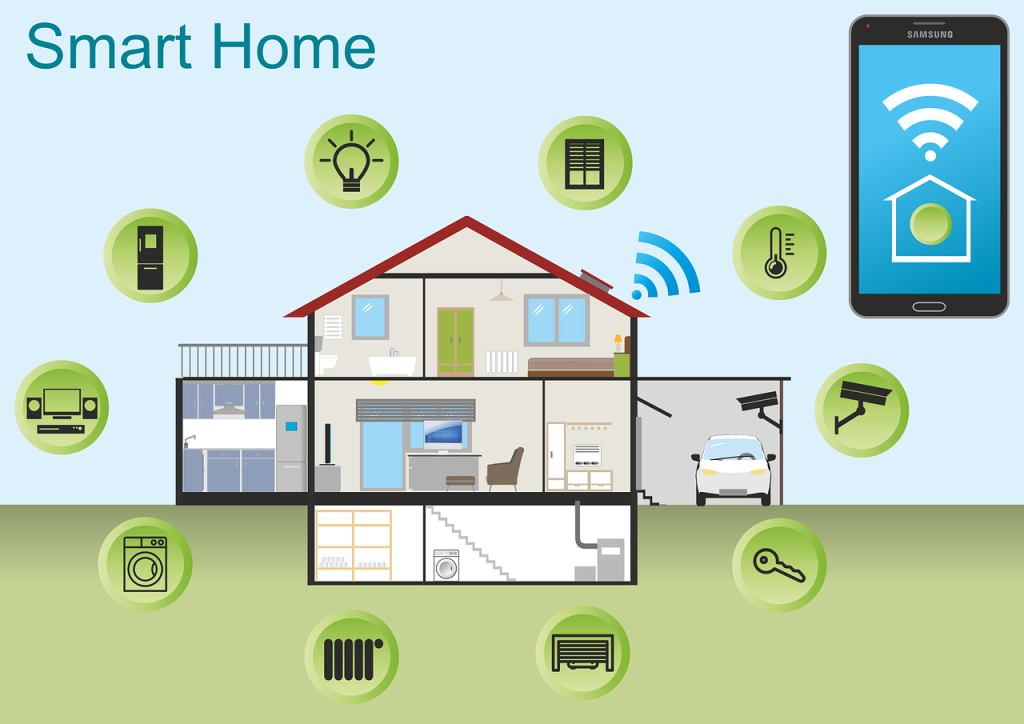
When you were a kid, the idea of a “smart home” probably felt like something out of a futuristic movie, like Back to the Future II or The Jetsons. While we may not have flying cars yet, we do have video calls, smart fridges, and voice-activated lights. However, even the most advanced tech can run […]
Eye-opening Insights from the 2023 Annual Cybersecurity Attitudes and Behaviors Report

In today’s world, digital connectivity shapes every aspect of our lives. The significance of cybersecurity cannot be emphasized enough. As technology progresses, so do the increasingly sophisticated threats in the digital landscape. Many times, we unknowingly make ourselves vulnerable to cyberattacks or online fraud. Risky habits like using weak passwords, neglecting security protocols, and adopting […]
Be Careful When Scanning QR Codes – There’s a New Scam Going Around!

QR codes are now ubiquitous in everyday life. You can spot them on restaurant menus, advertisements, and posters, seamlessly bridging the gap between offline and online interactions. They’re incredibly simple to use just scan with your smartphone camera, and you’re quickly directed to a website, a discount, a video, or other digital content. However, the […]
